by Adam Thierer & Andrea Castillo
Cybersecurity policy is a big issue this year, so we thought it be worth reminding folks of some contributions to the literature made by Mercatus Center-affiliated scholars in recent years. Our research, which can be found here, can be condensed to these five core points:
1) Institutions, societies, and economies are more resilient than we give them credit for and can deal with adversity, even cybersecurity threats.
See: Sean Lawson, “Beyond Cyber-Doom: Assessing the Limits of Hypothetical Scenarios in the Framing of Cyber-Threats,” December 19, 2012.
2) Companies and organizations have a vested interest in finding creative solutions to these problems through ongoing experimentation and they are pursing them with great vigor.
See: Eli Dourado, “Internet Security Without Law: How Service Providers Create Order Online,” June 19, 2012.
3) Over-arching, top-down “cybersecurity frameworks” threaten to undermine dynamism in cybersecurity and Internet governance, and could promote rent-seeking and corruption. Instead, the government should foster continued dynamic cybersecurity efforts through the development of a robust private-sector cybersecurity insurance market.
See: Eli Dourado and Andrea Castillo, “Why the Cybersecurity Framework Will Make Us Less Secure,” April 17, 2014.
4) The language sometimes used to describe cybersecurity threats sometimes borders on “techno-panic” rhetoric that is based on “threat inflation.
See the Lawson paper already cited as well as: Jerry Brito & Tate Watkins “Loving the Cyber Bomb? The Dangers of Threat Inflation in Cybersecurity Policy,” April 10, 2012; and Adam Thierer, “Technopanics, Threat Inflation, and the Danger of an Information Technology Precautionary Principle,” January 25, 2013.
5) Finally, taking these other points into account, our scholars have conclude that academics and policymakers should be very cautious about how they define “market failure” in the cybersecurity context. Moreover, to the extent they propose new regulatory controls to address perceived problems, those rules should be subjected to rigorous benefit-cost analysis.
See: Eli Dourado, “Is There a Cybersecurity Market Failure,” January 23, 2012.
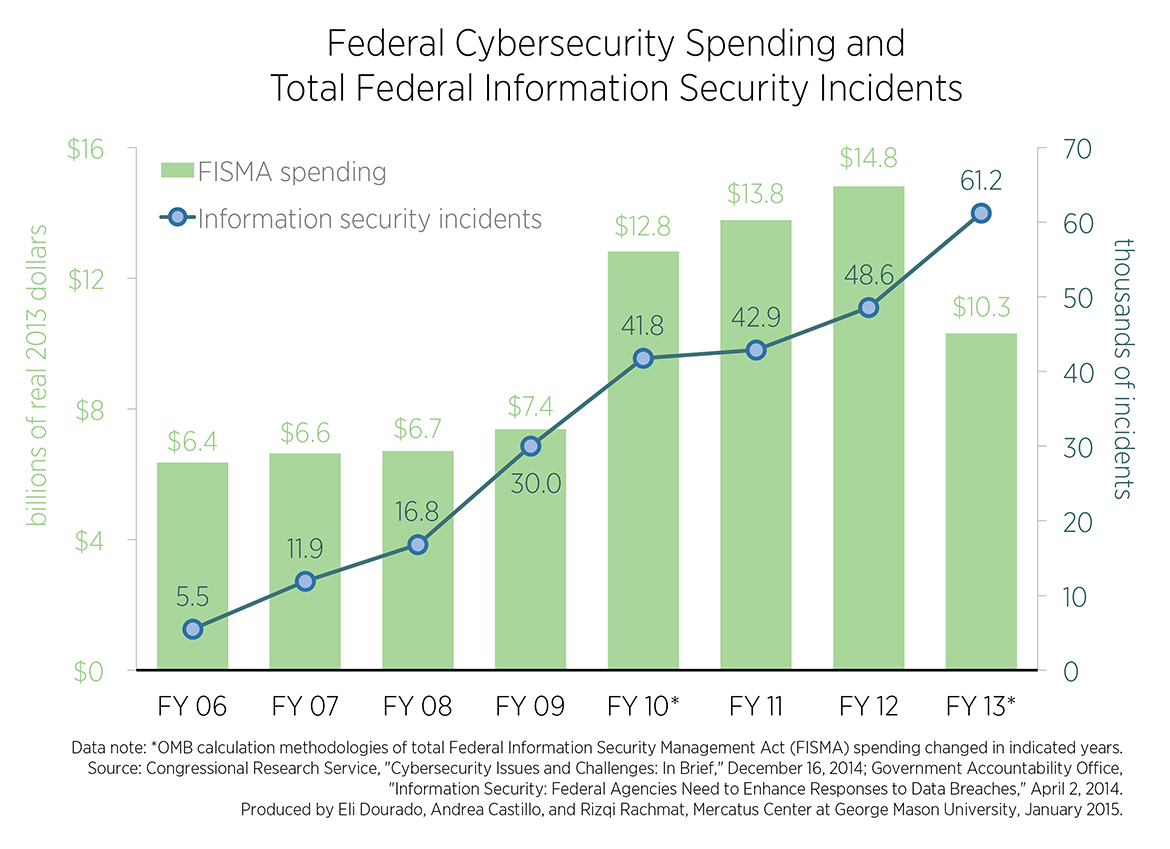 Developing cybersecurity policies—like the White House’s “Securing Cyberspace” proposal and the Senate Intelligence Committee’s risen-from-the-grave Cybersecurity Information Sharing Act (CISA) of 2015—prioritize government-led “information-sharing” among federal agencies and private organizations as a one-stop technocratic solution to the dynamic problem of cybersecurity provision. But, as Eli and Andrea pointed out in a Mercatus chart series from this year, the federal government’s own success with internal information-sharing policies has been abysmal for decades.
Developing cybersecurity policies—like the White House’s “Securing Cyberspace” proposal and the Senate Intelligence Committee’s risen-from-the-grave Cybersecurity Information Sharing Act (CISA) of 2015—prioritize government-led “information-sharing” among federal agencies and private organizations as a one-stop technocratic solution to the dynamic problem of cybersecurity provision. But, as Eli and Andrea pointed out in a Mercatus chart series from this year, the federal government’s own success with internal information-sharing policies has been abysmal for decades.
The Federal Information Security Management Act of 2002 compelled federal investment in IT security infrastructure along with internal information-sharing of system breaches and proactive responses among agencies. Apparently, this has not worked like a charm. The chart shows that reported federal breaches have risen by over 1000% since 2006 despite spending billions of dollars on agency systems and information sharing capabilities over the same time.
Many of the same agencies who would be imbued with power to coordinate information-sharing among private and government entities through CISA and other cybersecurity proposals were responsible for coordinating threat-sharing on the federal level. These are the National Institute of Standards and Technology (NIST), the Office of Management and Budget (OMB), and the Department of Homeland Security (DHS). Are we to believe these bodies will become magically efficient once they have more power to cajole the private sector?
Government Accountability Office (GAO) reports analyzing the failure of federal information security practices and threat coordination find that the technocratic solutions that look so perfectly rational and controlled on paper break down when imposed from above on employees that have no buy-in. The report concludes, “As we and inspectors general have long pointed out, federal agencies continue to face challenges in effectively implementing all elements of their information security programs.” Repeating the same failed policies in the private sector is unlikely to result in success.
Cybersecurity provision is too important of an issue to be left to brittle, technocratic policies with proven track records of failure. Rather, good cybersecurity policy will be grounded in an understanding of the incentives and norms that have allowed the Internet to develop and thrive as the system that it is today to target specific sources of failure.
Industry analyses find again and again that with cybersecurity, the problem exists between chair and keyboard—“human error,” not insufficient government meddling, is responsible for the vast majority of cyber incidents. Introducing more error-prone humans to the equation, as government cybersecurity plans seek to do, will only complicate the problem while neglecting the underlying factors that need addressing.
Cybersecurity will be an issue we continue to cover closely at the Mercatus Center Technology Policy Program.

 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.