My new book, 100 Plus, is about how science and technology will allow us to live longer and healthier – and how that will change the world. This topic may be newish for this site, but many of the key issues are not. What happens to economic growth in this tech revolution? How does innovation play a part in resolving problems such as environmental waste? Should we be worried about a divide between the haves and the have nots? I address all these questions and more, including the impact on religious institutions. The final chapter of the book details how leaders, including many in the traditional technology industry, are pushing ahead with reverse-engineering the human body – the next big thing.
Here is an excerpt of the book in the Wall Street Journal.
Hot-tempered police offers, pushover judges, and vague laws make for a dangerous combination. In July, a controversy erupted in Renton, Washington (a Seattle suburb) when the town’s police department launched a legal assault on an anonymous YouTube user for merely uploading a few sarcastic videos poking fun at the department’s scandals.
 In an op-ed in The Seattle Times, Nicole Ciandella and I explain what happened in Renton and discuss the saga’s implications for constitutional rights in the digital age:
In an op-ed in The Seattle Times, Nicole Ciandella and I explain what happened in Renton and discuss the saga’s implications for constitutional rights in the digital age:
According to Washington state law, a person is guilty of criminal “cyberstalking” if he makes an electronic communication using lewd or indecent language with the intent to embarrass another person. In other words, a Washingtonian who creates a raunchy email message, blog post or Web video to embarrass a foe isn’t just playing dirty; he’s technically breaking the law. One YouTube user recently learned this lesson the hard way.
Last month, the scandal-ridden Renton Police Department launched a criminal cyberstalking investigation against a YouTube user known only as “MrFuddlesticks.” The user had uploaded a series of lewd, animated videos poking fun at recent allegations of wrongdoing by Renton police officers. In one video, a character talks about his civilian superior’s lack of law-enforcement experience; in another, characters discuss the impropriety of a police officer who slept with a murder suspect.
Even though none of MrFuddlesticks’ videos mention the city of Renton or any police officers by name, Renton police managed to convince a county judge to issue a warrant to compel Google, YouTube’s parent company, to disclose identifying information about MrFuddlesticks’ accounts, including credit-card details and even contents of Gmail messages.
You can read the rest of the essay here. (For more on the controversy, see Jacob Sullum at Reason’s Hit & Run; also see Mike Masnick at Techdirt. For an exploration of the case’s constitutional implications, see Eugene Volokh at The Volokh Conspiracy.)
Here on the TLF, we’ve repeatedly cautioned lawmakers about the dangers of criminalizing cyberstalking (1, 2, 3, 4). Back in 2006, CNET’s Declan McCullagh explained why all Internet users should be worried about vague, overbroad cyberstalking laws. As the troubling actions of Renton’s finest illustrate, the potential for such laws to be abused is very real. Let’s hope lawmakers in Washington and in the numerous other states with cyberstalking laws on the books take a hard look at their laws.
On the podcast this week, Adam Thierer, Senior Research Fellow at the Mercatus Center at George Mason University in the Technology Policy Program, discusses his new paper, Kids, Privacy, Free Speech & the Internet: Finding the Right Balance. For kids, using the Internet has become second nature, but when sites that track a child’s online activity can raise privacy concerns. A number of well-intentioned lawmakers are introducing regulatory measures that aim to expand the Children’s Online Privacy Protection Act (COPPA). Thierer discusses the unintended consequences that could result from regulations, like mandatory age verification and an Internet “eraser button.” He proposes an alternative to regulation, which includes education and empowerment, placing importance on personal and parental responsibility.
Related Links
To keep the conversation around this episode in one place, we’d like to ask you to comment at the webpage for this episode on Surprisingly Free. Also, why not subscribe to the podcast on iTunes?
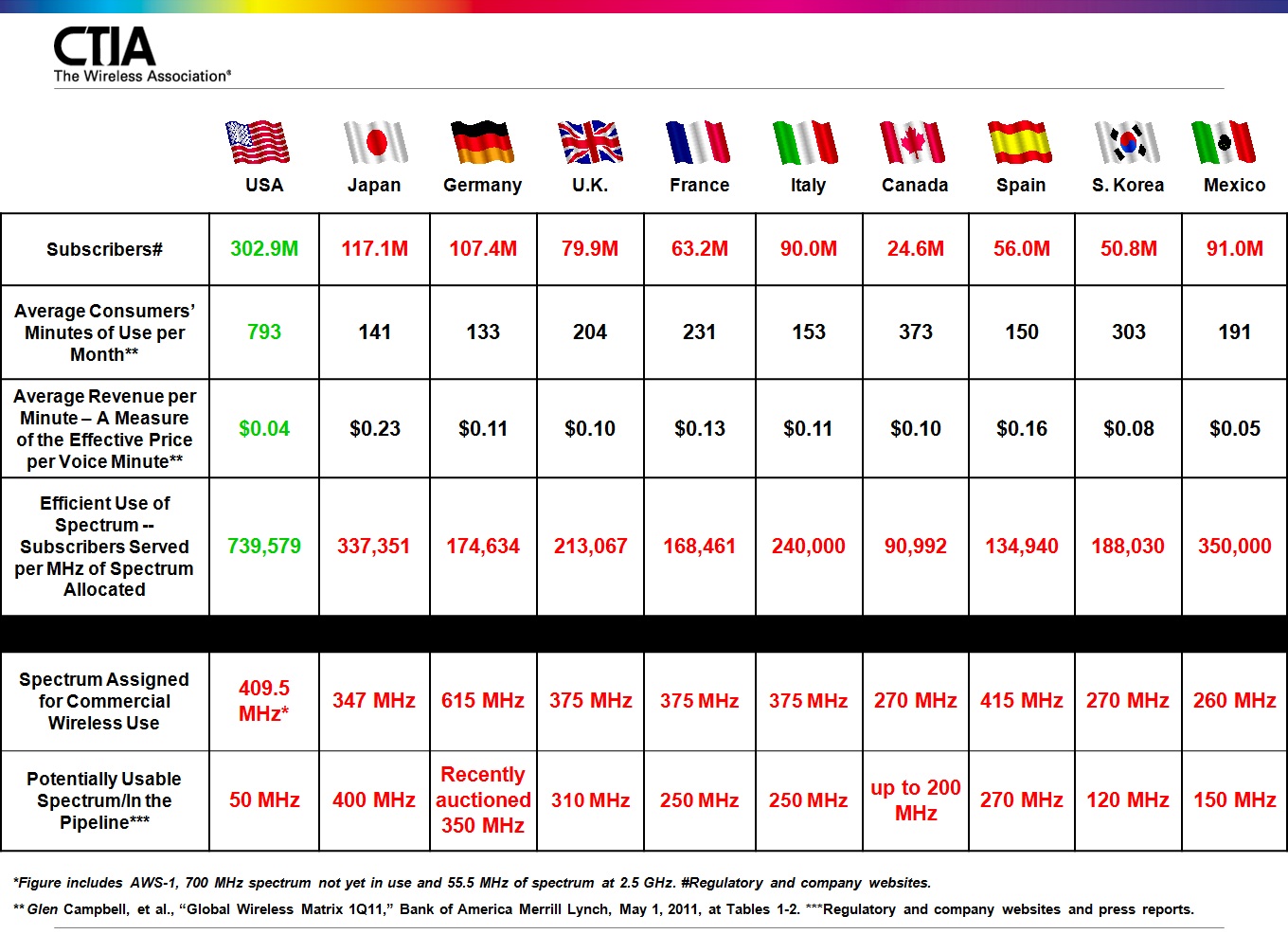
Here’s a terrifically useful chart from CTIA that offers some international wireless use and spectrum availability comparisons. [Click on chart to expand.] The average minutes of use and average revenue per minute differences are fairly staggering. But the really important takeaway from this chart is the last line, which depicts how little spectrum is dripping out of the faucet right now. Having just 50 MHz of “potentially usable spectrum in the pipeline” is troubling and needs to be addressed by policymakers immediately. America’s wireless demands continue to explode, but supply isn’t keeping up.
My latest Mercatus Center white paper is entitled “Kids, Privacy, Free Speech & the Internet: Finding The Right Balance.” From the intro:
Concerns about children’s privacy are an important part of [the ongoing privacy debate]. The Children’s Online Privacy Protection Act of 1998 (COPPA) already mandates certain online-privacy protections for children under the age of 13. The goal of COPPA was to enhance parents’ involvement in their children’s online activities and better safeguard kids’ personal information online. The FTC is currently considering an expansion of COPPA, and lawmakers in the House of Representatives introduced legislation that would expand COPPA and apply additional FIPPS regulations to teenagers. Some state-based measures also propose expanding COPPA
While well-intentioned, efforts to expand privacy regulation along these lines would cause a number of unintended consequences of both a legal and economic nature. In particular, expanding COPPA raises thorny issues about online free speech and anonymity. Ironically, it might also require that more information about individuals be collected to enforce the law’s parental-consent provisions. There are better ways to protect the privacy of children online than imposing burdensome new regulatory mandates on the Internet and online consumers. Education, empowerment, and targeted enforcement of unfair and deceptive practice policies represent the better way forward.
The paper can be downloaded on SSRN, Scribd, or directly from the Mercatus website at the link above.
 For CNET this morning, I offer five crucial corrections to the Protect IP Act, which was passed out of committee in the Senate back in May.
For CNET this morning, I offer five crucial corrections to the Protect IP Act, which was passed out of committee in the Senate back in May.
Yesterday, Rep. Bob Goodlatte, co-chair of the Congressional Internet Caucus, told a Silicon Valley audience that the House was working on its own version and would introduce it in the next few weeks.
Protect IP would extend efforts to combat copyright infringement and trademark abuse online, especially by websites registered outside the U.S.
Since Goodlatte promised the new bill would be “quite different” from the Senate version, I thought it a good time to get out my red pen and start crossing off the worst mistakes in policy and in drafting in Protect IP.
The full details are in the article, but in brief, here’s what I hope the House does in its version:
- Drop provisions that tamper with the DNS system in an effort to block U.S. access to banned sites.
- Drop provisions that tamper with search engines, indices, and any other linkage to banned sites.
- Remove a private right of action that would allow copyright and trademark holders to obtain court orders banning ad networks and financial transaction processors from doing business with banned sites.
- Scale back current enforcement abuses by the Department of Homeland Security under the existing PRO-IP Act of 2008.
- Focus the vague and overinclusive definition of the kind of websites that can be banned, limiting it to truly criminal enterprises.
Continue reading →
On the podcast this week, Ryan Calo, a scholar at Stanford’s Center for Internet and Society, discusses his new article in the Maryland Law Review entitled “Open Robotics.” Robots are frequently used in war, manufacturing, warehouse management, and even in surgery. Now, personal robots are poised to be the new explosive technology, and Calo anticipates their social effect to be on par with that of the personal computer. He discusses why he believes personal robots are more likely to thrive if they are built on an open model–rather than closed or proprietary framework–even though robots open to third-party tinkering may be subject to greater legal liability than closed, discrete-function robots. To protect open-model innovation, Calo recommends immunity for manufacturers of open robotic platforms for what end users do with these platforms, akin to the immunity enjoyed under federal law by firearms manufacturers and websites.
Related Links
To keep the conversation around this episode in one place, we’d like to ask you to comment at the webpage for this episode on Surprisingly Free. Also, why not subscribe to the podcast on iTunes?
Paul Vixie, a renowned Internet pioneer who runs the Internet Systems Consortium, has written an article in ACM Queue attacking “those who would unilaterally supplant or redraw the existing Internet resource governance or allocation systems.” The publication of this article is a sign of a growing, important debate around the reform of IP address registries in the age of IPv4 exhaustion.
Vixie defends the Regional Internet Registries monopoly on IP address registration services and its current, needs-based policies toward address transfers. I am sure that Paul sincerely believes in the arguments he makes, but it’s also true that Vixie is the chairman of the Board of The American Registry for Internet Numbers (ARIN), the regional address registry for North America. When Vixie argues that ARIN’s exclusive control over Whois and address transfer services is beneficial and “in the physics” he is also defending the authority and revenue model of his own organization against a perceived threat.
And that takes us to another relevant fact. The argument Vixie makes is cast in generalities, but he is really attacking a specific firm, a holding company known as Denuo. Denuo has formed both a secondary marketplace called Addrex for the legitimate trading of IPv4 number blocks, and an IP Address Registrar company known as Depository. Let’s set aside Depository for the moment (I will come back to it) and concentrate on Addrex, which has become the first end-to-end platform for legacy address holders to sell their IPv4 number blocks. Famously, Addrex scored a major success as the intermediary for the Nortel-Microsoft trade. But Nortel-Microsoft was unusually visible because it had to go through bankruptcy court. Is anything else happening? I spoke to Addrex’s President Charles Lee since then to find out. “We are very busy signing up a growing number of global corporate and governmental customers to sell their unused assets,” he said. I asked him what the buyer side of the marketplace was beginning to look like and he said “Our value proposition to large Asian network operators has resonated quite effectively and we expect to enter into many agreements with them over the coming months.” Surely Vixie and the ARIN Board have gotten wind of this. So when Vixie begins a public attack on this company and its business model, he is signaling to the rest of us that ARIN is worried. Continue reading →
The Technology Liberation Front (TLF) turned 7 yesterday. We got underway on Aug 14, 2004 with this post. For more of the backstory of how things got started, see this post upon the occasion of our 5th anniversary. We’re now up to 5,800+ posts and we’ve received almost 34,400 comments on those entries.
The goal of the TLF was to bring together liberty-loving technology policy analysts who were concerned about rising calls for government control of the Internet, digital technologies, and media and communications platforms. While we’ve slowed down a bit here in recent years, I’m quite proud of what we’ve done over the years to advance that vision and want to I thank everyone involved in the effort and all those readers who found it worth their time to stop by.
We’ll keep fighting the good fight for technology and information freedom!
Republished from the Daily Caller
U.K. Prime Minister David Cameron has declared “everything necessary will be done to restore order” in Britain’s riot-racked cities. With respect to the right honorable gentleman, what distinguishes free from unfree societies is not order, but ordered liberty. As the great Tory philosopher Edmund Burke taught, reconciling liberty and order is the fine art of democratic statecraft. Tweaking that balance as technology evolves requires the most careful and judicious deliberation. Only where cooler heads prevail can ordered liberty thrive.
Cameron’s government has hesitated to escalate physical force with rubber bullets and water cannons, lest they lend moral sanction to the brutal tactics used by China and in the Middle East to suppress dissent. Yet however noble his intentions, Cameron could do more to undermine ordered liberty with “bloodless” measures targeting social media services like Twitter and Facebook, and improperly using photo identification.
Cameron, who championed Internet-driven revolutions in Egypt and Tunisia, told Parliament that the “free flow of information can be used for good, but it can also be used for ill.” His vague response: “We are working with the police, the intelligence services and industry whether it will be right to stop people communicating via these websites and services.”
So far, the only clear call for shutting down social media outright came from a Labour MP, not Cameron’s Tories. David Lammy, who represents the London neighborhood where rioting began, has demanded the suspension of BlackBerry Messenger (BBM) service for “helping rioters outfox Police.” Such a response befits Beijing, not Britain, the birthplace of ordered liberty.
Free societies can and should silence those who incite acts of violence — but not by shutting down speech platforms for all users. Even America’s speech-protective First Amendment allows punishment of speech that is “directed to inciting or producing imminent lawless action and is likely to incite or produce such action.” That standard protects legitimate expression without preventing prosecution of those individuals stoking and organizing riots. The same standard should determine when government may properly force social media systems to take down seditious posts, photos and videos. Continue reading →

 In an
In an 

 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.