I recently subscribed to the Software Freedom Law Center’s podcast, and just finished listening to episode 5, in which SFLC director Eben Moglen talks about the history of copyright and patent law. It’s a bracing talk that’s bound to be controversial with a lot of people. And in particular, it’s framed in a way that’s not at all calculated to appeal to libertarians. With what I suspect is deliberate irony, he even uses the phrase “from each according to his ability, to each according to his needs” to describe what free software is all about.
Nevertheless, what struck me in listening to his talk was that even though Moglen’s rhetoric seems almost calculated to alienate libertarians used to aligning themselves with the political right, it’s awfully hard for libertarians to actually object to the substance of what the SFLC and the Free Software Foundation are doing. A quarter century ago, when Richard Stallman was upset with the trend
toward away from free software, he didn’t run to Congress seeking legal changes. Rather, he sat down and started building an alternative. One that we know today as the GNU/Linux operating system. He did so without a penny of government support, and without expropriating any resources from his proprietary competitors.
And in the process, he provided a powerful counterexample to many of the standard tropes of copyright and patent debates. In a world where some of the most popular websites on Earth are built on the LAMP stack, it’s awfully hard to argue with a straight face that creativity will only happen if creators are given monopoly rights in their creations. The rest of us can argue until they’re blue in the face about what a world with weaker copyright or patent protections would look like, but Stallman and company have bypassed that debate entirely by offering an existence proof of what an alternative world would look like. It’s awfully hard to argue something can’t happen when it obviously has.
Which I think is what gives Eben Moglen the credibility to deploy what I might otherwise regard as absurdly overwrought rhetoric. Most revolutionaries preach about the utopia that will exist in the future. In contrast, Moglen is talking about a utopia that’s being built as we speak. And happily for libertarians, it’s a utopia that’s being built without a shot being fired, or a tax dollar being spent.
I have been asked to testify at a hearing of the House Committee on Oversight and Government Reform on Thursday, March 19, 2009. It is entitled “Preventing Stimulus Waste and Fraud: Who Are the Watchdogs?” [PDF] and it will focus on accountability for stimulus spending. I will talk about how third parties can build interesting tools to help citizens find and sort spending, jobs, and performance information if only government provides the data in a complete, timely, and standardized manner.
As a way to illustrate the concept of crowdsourcing to the Committee (and to make myself seem smarter than I am) I thought I would ask you all to help me edit the testimony. I have set up a wiki with my draft written testimony on it. Please feel free to add anything I may have missed and to make any changes you see fit.
To contribute, you will need to click the “Edit” button and then ask for permission to edit the wiki (it doesn’t let me give automatic access). I will grant you permission immediately. My testimony is due by C.O.B. tomorrow, and I will incorporate all changes that I would feel comfortable testifying to.
Thanks for your help!
 As noted in the first installment of our “Privacy Solution Series,” we are outlining various user-empowerment or user “self-help” tools that allow Internet users to better protect their privacy online-and especially to defeat tracking for online behavioral advertising purposes. These tools and methods form an important part of a layered approach that we believe offers an effective alternative to government-mandated regulation of online privacy.
As noted in the first installment of our “Privacy Solution Series,” we are outlining various user-empowerment or user “self-help” tools that allow Internet users to better protect their privacy online-and especially to defeat tracking for online behavioral advertising purposes. These tools and methods form an important part of a layered approach that we believe offers an effective alternative to government-mandated regulation of online privacy.
In the last installment, we covered the privacy features embedded in Microsoft’s Internet Explorer (IE) 8. This installment explores the privacy features in the Mozilla Foundation’s Firefox 3, both the current 3.0.7 version and the second beta for the next release, 3.5 (NOTE – The name for the next version of Firefox was just changed from 3.1 to 3.5 to reflect the large number of changes, but the beta is still named 3.1 Beta 2). We’ll make it clear which features are new to 3.1/3.5 and those which are shared with 3.0.7. Future installments will cover Google’s Chrome 1.0, Apple’s Safari 4, and some of the more useful privacy plug-ins for browsers . The availability and popularity of privacy plug-ins for Firefox such as AdBlock (which we discussed here), NoScript and Tor significantly augments the privacy management capabilities of Firefox beyond the capability currently baked into the browser. In evaluating the Web browsers, we examine:
(1)
cookie management;
(2)
private browsing; and
(3)
other privacy features
Continue reading →

Better not be offering incentives!
As I previously reported, the DC Circuit recently upheld a decision by the FCC to forbid customer retention practices used by Verizon to incentivize its customers to stay with the carrier rather than leaving for a VOIP provider. In the earlier post, I analyzed the bad economics of the FCC’s ban. In this post, as promised, I go into greater detail on the court’s decision affirming the FCC.
The latest issue of the Center for Internet and Society’s publication, Packets, has arrived and with it my summary of the case. The Packets piece provides a more neutral (but detailed) summary of the DC Circuit’s decision, without much analysis.
The big question before the court was whether what the FCC did was really pursuant to the Telecommunications Act, which forbids a telco “that receives or obtains proprietary information from another carrier for purposes of providing any telecommunications service” from using the information for a marketing purpose. If not, then essentially the FCC just went AWOL; instead of enforcing the law, as it is supposed to, it simply made its own law.
Indeed, that is exactly what happened here. The natural reading of the language, as the court admits, is contrary to the FCC’s ruling. To use an example employed by the court, when one says “Joe received information from Mary for purposes of drafting a brief,” the court reasoned, “it is overwhelmingly likely that the speaker expects Joe to do the drafting.” But Verizon is getting the information from other telcos
not in order to provide their customers with phone service, but to cut off service. It is the competitors who are using the information to provide phone service. Mary is drafting the brief, so the statute doesn’t apply! The court never fully explains why it refuses to limit the statutory language to its natural meaning – saying only that one could grammatically read it the other way. Continue reading →
I’ve already laid out my own reactions to Google’s roll-out of an “interest based advertising” (IBA) program here. In a nutshell, I applauded Google setting a new “gold standard” in user empowerment by providing:
- Notice in their IBA-targeted ads of who’s paying for the ad and the fact that Google is serving it; and
- A link to a powerful “Ad Preference Manager” that allows users to:
- See and modify the “digital dossier” (to use the fearmonger’s term) of interests associated with the cookie on their computer; and
- Opt-out of tracking for IBA purposes.
But as I predicted, despite these pro-privacy features (and despite the fact that other major companies such as Yahoo! and Microsoft already have IBA programs), a number of privacy advocacy organizations are attacking Google for daring to enter the IBA (or “online behavioral advertising”) business at all. I’ll have much more to say about the criticism of Google’s new Ad Preference Manager soon, especially coming from Marc Rotenberg of EPIC (a “disaster“) and Jeff Chester of CDD—precisely the sort of the “paroxysms of privacy hysteria” I predicted.
But first, the criticism from Ari Schwartz of the Center for Democracy & Technology requires a response today. At its best, CDT plays a vital role in calling corporations to continually raise the bar on privacy. My own think tank, the Progress & Freedom Foundation, works closely with CDT on many issues, such as advocating user empowerment through technological means as a constitutionally “less restrictive” way of protecting children than government censorship.
Here’s what Ari had to say: Continue reading →
Theories constitute the technology of academia. They give us eggheads the tools we need to get our work done, just as computers serve programmers and DNA sequencing serves bioengineers. I trust that TLF’s readers won’t think me too far off-topic, then, if I cite a new approach to consent theory, something that should interest anyone who cares about the fundamental reasons for valuing of liberty. Here’s a snapshot of the theory:
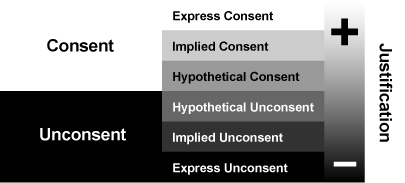
One hopes not. But the White House’s 60-day review of cyber security, ongoing now, could set the stage for it.
In a TechKnowledge piece out today, I argue against federal responsibility for private cyber security. A common law liability regime is the best route to discovering and patching security flaws in all the implements of our information economy and society.
The smarties at the Center for Information Technology Policy at Princeton recently sat down to discuss these issues too.
Today, it was my great privilege to guest lecture at Princeton University’s Center for Information Technology Policy. Under the leadership of Ed Felten, who also runs the excellent “Freedom to Tinker” blog, the CITP has quickly become one of America’s premier institutions in the field of IT policy matters. David Robinson, who some of you will remember from his days as an editor at The American, serves as associate director of the CITP program and was kind enough to invite me to speak. And our own Tim Lee is currently studying there as well. I wish I was smart enough to get into that program!
The topic of my talk was “The Future of the First Amendment in an Age of Technological Convergence” and I used the opportunity to create a narrated video of this presentation, which I have made to several other groups through the years. In this presentation, I talk about “America’s First Amendment Twilight Zone,” which refers to the fact that identical words and images are being regulated in completely different ways today depending on the mode of transmission. This illogical and unfair situation could eventually threaten the Internet, video games, and all new media with many of the misguided regulations that have long been imposed on broadcast television and radio operators. In my presentation, which you can watch below, I make the case for changing our First Amendment regime to ensure “bit equality”; all speech and media platforms should be accorded the gold standard of First Amendment protection.
http://www.youtube.com/v/xJo3tVMScyI&hl=en&fs=1
Continue reading →
Google’s new “Interest Based Advertising” (IBA) program represents the company’s first foray into what is generally called “Online Behavioral Advertising” (OBA): In order to deliver more relevant advertising, Google will begin tailoring ads delivered through AdSense on the Google Content Network (GCN) and YouTube.com (but not Google.com). This tailoring will be based on a profile of each user’s interests created by tracking their browsing activity across sites that use AdSense-but not search queries or other user information. Until now, (i) AdSense has delivered essentially “contextual” advertising by choosing which ad to display on a page based on an algorithmic analysis of keywords on that page; and (ii) Google has tracked users’ browsing only for analytics purposes-to limit the number of times a user sees a particular ad (to prevent overexposure) and to allow sequencing of ads in campaigns where one ad must follow another.
Google is sure to be attacked for crossing a “line in the sand” drawn by some privacy advocates between contextual and behavioral advertising-even though Google’s closest competitor, Yahoo!, already offers a similar program, and the concept in general is hardly new. Google’s position as the leading search engine and third party ad-delivery network will no doubt cause paroxysms of privacy hysteria among those who consider targeted advertising inherently invasive, unfair or manipulative.
But those whose first priority is advancing consumer privacy, not advancing a political or regulatory agenda, should applaud Google for excluding sensitive categories and for putting the new Ad Preference Manager at the core of the company’s new IBA program. The Ad Preference Manager sets a new “gold standard” for implementing the principles of Notice and Choice, which have formed the core of both OBA industry self-regulation and the various regulatory proposals made in recent years. Indeed, Google has done precisely what Adam Thierer and I have called for: giving consumers more granular control over their own privacy preferences by developing better tools.
Continue reading →

 As noted
As noted 

 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.