In late June, the Federal Communications Commission (FCC) opened a Notice of Inquiry and Notice of Proposed Rulemaking regarding “Sponsorship Identification Rules and Embedded Advertising” (MB Docket No. 08-90). Basically, it’s an inquiry into the product placement and embedded advertising practices on television. Some at the FCC want such practices regulated.
PFF filed comments in the matter today. Ken Ferree and I argue that that FCC regulation of such advertising practices would be unnecessary and unwise. “If the Notice demonstrates anything,” we argue, “it is that a majority of the current Commissioners live in a world wholly alien and unfamiliar to most Americans; indeed, a world long forgotten if it ever existed.” We continue:
The Notice alludes menacingly to new, “subtle and sophisticated means” of commercial messaging, to “sneaky commercials” (quoting a senescent order topped with nearly fifty-years of dust) and to “vindicat[ing]” the policy goals of the Communications Act – as if the FCC must exact vengeance on those who would try – horror of horrors – to sell goods and services to the American public. The melodramatic tone of the Notice is intended, of course, to set the stage for the Commission’s latest effort to micromanage the free marketplace of ideas, i.e., the media. Only by portraying “embedded” advertising as something new and nefarious can the Commission hope to justify a new portfolio of intrusive and burdensome speech regulations in the name of preserving the “public’s right to know who is paying to air commercials or other program matter on broadcast television and radio and cable.”
And, as we make clear in the filing, we don’t buy the argument that the public are nothing more than mindless sheep:
Continue reading →
I’m getting married next Spring, and I’m currently negotiating the contract with our photographer. The photography business is weird because even though customers typically pay hundreds, if not thousands, of dollars up front to have photos taken at their weddings, the copyright in the photographs is typically retained by the photographer, and customers have to go hat in hand to the photographer and pay still more money for the privilege of getting copies of their photographs.
This seems absurd to us, and we’ve found a photographer who’s willing to give us our images in high-resolution digital form along with a copyright release to make our own copies of the images. I’m currently researching language for the copyright release, and the advice offered on the subject—mostly by photograhers—strikes me as excessively restrictive. Photographers seem to regard it as extremely important to micro-manage their customers’ use of the images they take, giving them glorified permission slips that only allow the pictures to be used for personal, non-commercial use. There seems to be a consensus that this is important, but I don’t really understand why. It’s not like pictures of my wedding are going to have tremendous commercial value, and allowing us to commercially exploit the photos won’t prevent our photographer from doing so as well (which is fine by me).
Anyway, all of the example copyright releases on the web are unnecessarily restrictive, so what I think I’m going to propose to our photographer is language derived from the creative commons license, like so:
the photographer will provide to the undersigned a worldwide, royalty-free, non-exclusive, perpetual (for the duration of the applicable copyright) license to exercise the rights in all images to: (1) Reproduce the images, to incorporate the images into one or more Collections, and to Reproduce the images as incorporated in the Collections; (2) to create and Reproduce Adaptations; (3) to Distribute and Publicly display the images including as incorporated in Collections; and, (4) to Distribute and Publicly display Adaptations.
If there are any lawyers in the audience, please let me know if you have any suggestions for improvement.
Also next time a lawyer at Creative Commons has some spare cycles, it would be great if he or she could write a guide to the copyright issues around wedding photography (or for-hire photography more generally). Ideally, CC should provide a how-to guide for hiring a photographer in a way that ensures that all photos taken will wind up under the appropriate CC license. This might include explanations of the key legal pitfalls and example language that could be placed directly into the photographer’s contract. It would also be good if it included a page that customers can point their photographers, explaining what a CC license is and why the photographer shouldn’t freak out about having some of his or her photographs released under it. In our digital age, it’s absurd that most people have to ask permission to make copies of pictures of their own wedding.

Over the past week there’s been a lot of Google blogging (here, here, here…) on TLF, so now it’s my turn. And I’ll defer to the post of my colleague Mark Blafkin on the ACT blog, provocatively titled Why is Google Pointing that Gun at its Foot?
Here’s a snippet:
Google has not yet learned that when you’re under antitrust scrutiny, EVERYTHING YOU DO is going to be analyzed through that lens. Every move your company makes will communicate something to the regulators, partners, customers, and competitors that are now watching you more closely. The last thing you want to do is give regulators more ammunition. At times, this may require changing decision making processes throughout the company, even in seemingly unrelated aspects of business.
ACT was engaged in the Microsoft antitrust case. Google can learn a lot from Microsoft’s battle, and by the way governments characterized what’s “anti-competitive.”
From triumph to terror—that’s the likely emotional rollercoaster of the denizens of the “/b” message board on the 4chan website who hacked into Gov. Sarah Palin’s email account earlier this week. The toasts of the left-learning Internet on Tuesday, by this morning they knew themselves to be in the crosshairs of the FBI and Secret Service.
Next stop: jail. That’s the law, and it’s a fair punishment for digital breaking and entering.
According to British tech tabloid The Register, the hackers accessed Palin’s Yahoo account by way of a proxy, relaying all traffic through it to cloak their identities. The proxy’s owner promises to make his log data available to authorities, and it’s probably only a matter of time before that leads to living, breathing (nervous, sweating?) people.
The most likely charge is hacking. Federal law prohibits virtual trespassing for the purposes of stealing information. So cracking the password to a governor’s email account and perusing her messages is a clear violation. The punishment: criminal fines and imprisonment of up to 5 years.
Throw in a few conspiracy offenses—according to reports, a slew of “/b-tards” were in on the act—and the prison term could double.
No, going after a major party’s vice presidential candidate was not smart: Police and prosecutors put extra effort into famous crimes.
As for the media publishing Palin’s emails and family photos, shame on them, but it’s not against the law. In Bartnicki v. Vopper, the Supreme Court held that they have a First Amendment right to publish materials of public importance, even if illegally obtained, so long as the media doing the publishing committed no wrong itself.
But just because it’s legal doesn’t mean it’s right. No one deserves to have their private correspondence stolen (not, as per the AP, “leaked”) and posted online for the world to see. It speaks to Palin’s classiness that nothing objectionable—not even a cuss—has come to light. Too bad that the press and online gossip-mongers don’t share that trait and take the material down.
And so the series continues. The Washington Post reports that the Department of Justice has just released “a scathing report” finding that over a 5-year period the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) “lost dozens of weapons and hundreds of laptops that contained sensitive information.” The DOJ’s Inspector General Glenn A. Fine found that 418 laptop computers and 76 weapons were lost. According to the report:
Yesterday’s report showed that ATF, a much smaller agency than the FBI, had lost proportionately many more firearms and laptops. “It is especially troubling that that ATF’s rate of loss for weapons was nearly double that of the FBI and [Drug Enforcement Administration], and that ATF did not even know whether most of its lost, stolen, or missing laptop computers contained sensitive or classified information,” Fine wrote. […]
Many of the missing laptops contained sensitive or classified material, according to the report. ATF began installing encryption software only in May 2007. ATF did not know what information was on 398 of the 418 lost or stolen laptops. The report called the lack of such knowledge a “significant deficiency.” Of the 20 missing laptops for which information was available, ATF indicated that seven — 35 percent — held sensitive information. One missing laptop, for example, held “300-500 names with dates of birth and Social Security numbers of targets of criminal investigations, including their bank records with financial transactions.” Another held “employee evaluations, including Social Security numbers and other [personal information].” Neither laptop was encrypted.
The findings regarding lost weapons were equally troubling, if not a bit humorous:
Continue reading →
In the beginning, there was Obamamania:
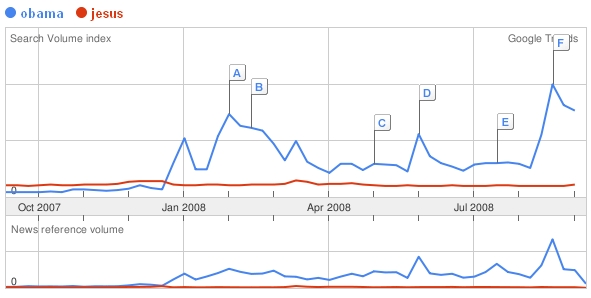
Then there was Palinmania:
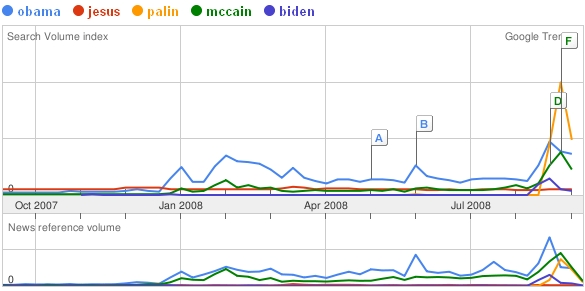
Poor Joe Biden. He gets fewer Google searches than that Jesus guy–whatever he‘s running for.
Google Trends is a nifty proxy for measuring public interest in a very narrowly defined subject. The examples above show “Search volume” (the total number of Google search queries for each keyword) and “News reference volume” (the same for news stories) for the last twelve months in the U.S. The lettered boxes indicate news stories tagged by keyword–which I have omitted from this screenshot for the sake of simplicity.
Wow. Mike Masnick writes about NASA’s plan to auction off some of its patent portfolio to the private sector. When I read this I had to do a double-take: NASA has a patent portfolio?
This is absurd. The purpose of patent law is to promote the progress of the useful arts by giving inventors an incentive to invent. NASA engineers already have an incentive to invent: they’re being paid taxpayer dollars to do so. Accordingly granting patents to NASA is a pure dead-weight loss to the economy. It restricts the free flow of ideas with no offsetting benefit from improved incentives. Indeed, this is precisely why the copyrights on government-created works are immediately placed in the public domain.
Why isn’t there a similar doctrine in place for patent law? I can’t see any reason government agencies should be allowed to apply for patents in the first place, but if they are going to do so, they should be placed in the public domain the same way copyrights are. How can it be legal for a government agency to use taxpayer money to perform research and then obtain patents that effectively prohibit most taxpayers from using the results of that research? If I helped pay for research, I should be free to use the results.
 “Buzz Out Loud,” one of my favorite podcasts, disappoints me from time to time, specifically when the good folks at CNET decide to bash broadband companies and call them “jerks” and “evil.”
“Buzz Out Loud,” one of my favorite podcasts, disappoints me from time to time, specifically when the good folks at CNET decide to bash broadband companies and call them “jerks” and “evil.”
So goes Episode 809 of Buzz Out Loud. Molly Wood, Jason Howell, and guest host Don Reisinger declare AT&T’s decision to throttle U-Verse (as reported by Ars-Technica) to be just another dumb thing that stupid broadband companies do.
One of their reasons for saying so is that AT&T’s U-Verse is fiber, but that’s not true. U-Verse uses fiber to feed VRADs, or Video Ready Access Devices, that take that fiber and feed its signal out over legacy copper wires, in a sort of DSL adapted-to-video hybrid.
When you get the facts wrong, your analysis is bound to be bad.
Continue reading →
 None other than Sci-Fi author, civil libertarian, blogger, activist, and TLF commenter Cory Doctorow drops in at the Bureaucrash Podcrash (that’s a podcast for “crashers”) to discuss his new book Little Brother.
None other than Sci-Fi author, civil libertarian, blogger, activist, and TLF commenter Cory Doctorow drops in at the Bureaucrash Podcrash (that’s a podcast for “crashers”) to discuss his new book Little Brother.
Austin Grossman’s review of the book for the New York Times remarks:
An entertaining thriller and a thoughtful polemic on Internet-era civil rights, “Little Brother” is also a practical handbook of digital self-defense. Marcus’s guided tour through RFID cloners, cryptography and Bayesian math is one of the book’s principal delights. He spreads his message through a secure network engineered out of Xbox gaming consoles, to a tech-savvy youth underground (we are now post-nerd, I learned — hipsters and social networking experts have replaced the unwashed coders of yore).
We at TLF may disagree with Mr. Doctorow on a number of policy issues, but I must admit that he’s a talented writer. I bought Cory’s Overclocked: Stories of the Future Present, a collection of short stories, at Capital Books here in DC and read it cover to cover by the end of that weekend. A great read available free in digital form at Cory’s Craphound.
Just FYI, the latest update of my booklet on “Parental Controls and Online Child Protection: A Survey of Tools & Methods” is now live. The new version, Version 3.1, provides minor updates to all sections of the book and a new appendix of relevant research in the field. I issue major updates early each year and 1 or 2 tweaks during the course of the year to reflect the evolution of the parental control and online child safety market and debate. 
For those not familiar with the report, it explores the market for parental control tools, rating schemes, education efforts, and initiatives aimed at promoting online child safety. I believe that the parental controls and content management tools cataloged in the report represent a better, less restrictive alternative to government regulation. As I conclude after evaluating that state of the market: “There has never been a time in our nation’s history when parents have had more tools and methods at their disposal to help them decide what constitutes acceptable media content in their homes and in the lives of their children.”
The report is available free-of-charge on the PFF website, and the previous editions of the report are housed there too in case you want to see how it has evolved over the past two years. For those interested in taking a quick look at the report, I have embedded it down below the fold as a Scribd file. Finally, as is always the case, I encourage readers to send me updates and suggestions for how to improve the report and I will incorporate them into future versions.
Continue reading →




 “Buzz Out Loud,” one of my favorite podcasts, disappoints me from time to time, specifically when the good folks at CNET decide to bash broadband companies and call them “jerks” and “evil.”
“Buzz Out Loud,” one of my favorite podcasts, disappoints me from time to time, specifically when the good folks at CNET decide to bash broadband companies and call them “jerks” and “evil.” None other than Sci-Fi author, civil libertarian, blogger, activist, and TLF commenter Cory Doctorow drops in at the
None other than Sci-Fi author, civil libertarian, blogger, activist, and TLF commenter Cory Doctorow drops in at the 
 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.