By Eric Beach and Adam Marcus
In the previous entry in the Privacy Solutions Series, we described how privacy-sensitive users can use proxy servers to anonymize their web browsing experience, noting that one anonymizer stood out above all others: Tor, a sophisticated anonymizer system developed by the Tor Project, a 501(c)(3) U.S. non-profit venture supported by industry, privacy advocates and foundations, whose mission is to “allow you to protect your Internet traffic from analysis.” The Torbutton plug-in for Firefox makes it particularly easy to use Tor and has been downloaded over three million times. The TorBrowser Bundle is a pre-configured “portable” package of Tor and Firefox that can run off a USB flash drive and does not require anything to be installed on the computer on which it is used. Like most tools in the Privacy Solutions series, Tor has its downsides and isn’t for everyone. But it does offer a powerful tool to privacy-sensitive users in achieving a degree of privacy that no regulation could provide.
Why Use Tor?
The Tor Project identifies its users as parents, militaries, journalists, law enforcement offers, activists, whistleblowers, and others. But on a high level, Tor addresses essentially four problems:
(1) Outbound blocking of internet traffic by IP or domain name. Countries, businesses, and Internet service providers may block web-users from accessing certain IPs associated with domain names that are deemed inappropriate. For example, access to certain domain names from inside some United Stated Federal government computer networks is restricted, some companies block pornography and some governments may censor access to some websites.
(2) Blocking of Internet traffic based upon content analysis. Rather than simply relying on website blacklists, many countries use content-based filtering to prevent individuals from seeking out information deemed undesirable. For example, the Chinese government censors searches for “falun gong” through packet inspection and analysis.
(3) ISP traffic logging. With the increased use of deep packet inspection, some privacy-sensitive Internet users worry that Internet service providers may be capable of logging the online activity of millions of Americans, and providing that information to governments or other third parties (lawfully or otherwise).
(4) Government monitoring. With the United States government’s pervasive surveillance of the electronic activities of Americans, some citizens understandably desire to protect their First Amendment right to anonymously send and receive information-i.e., without the government being able to determine their identity.
How Tor Works
The general web data flow online looks something like this:
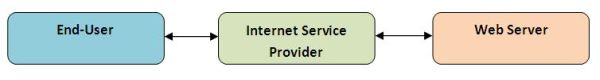
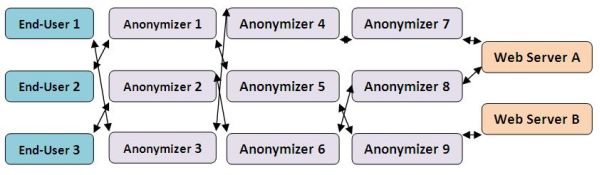
As we mentioned in our piece about anonymizers, a sophisticated anonymizer can obscure the identity of any one web user by pooling requests from large numbers of users across a “daisy chain” of proxy servers-thus effectively anonymizing the user’s identity, like so:
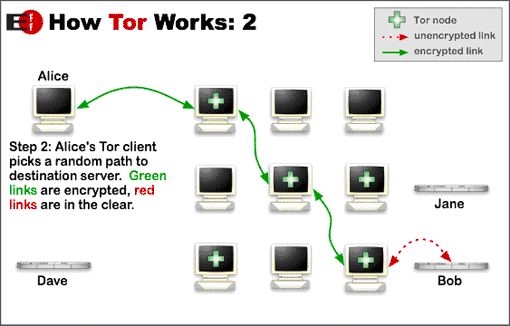
Tor works somewhat differently: Rather than simply trying to achieve “anonymity in a crowd” (of other web users using the network), Tor’s “client software” (e.g., TorButton) picks a random path through a network of other “Tor nodes” (users of Tor) for every request sent from the user’s computer. As the Tor Project explains:
Tor helps to reduce the risks of both simple and sophisticated traffic analysis by distributing your transactions over several places on the Internet, so no single point can link you to your destination. The idea is similar to using a twisty, hard-to-follow route in order to throw off somebody who is following you – and then periodically erasing your footprints. Instead of taking a direct route from source to destination, data packets on the Tor network take a random pathway through several relays that cover your tracks so no observer at any single point can tell where the data came from or where it’s going.
Tor thus achieves a high degree of anonymity, relying “not on the trustworthiness of individual servers but rather on the network design, which prevents a given router from knowing both the origin and the destination or even which other routers it would need to cooperate with to get that information.”
The following chart from the Tor Project’s more extensive explanation conveys the basics:
How to Install Tor
As mentioned above, Firefox users can install the TorButton plug-in, which will allow users to turn Tor on or off as desired.
The Tor Project also offers TorBrowser, an all-in-one bundle of the portable edition of Firefox (which can be carried along with all its settings on a USB stick or CD) pre-configured with the Tor plug-in. There is also a version of TorBrowser that includes the Pidgin instant messaging client, for those who also want to protect their instant messaging. Set-up takes less than three minutes and is just the thing for those trying to stay “one step ahead of The Man.” For more help on how to install the TorBrowser, click here or here.
Downsides/Risks of Tor
Speed. The biggest downside of using Tor is its slowness, which occurs for three reasons:
- Tor transports data among many intermediary nodes. Just as it takes considerably longer to drive from Los Angles to San Francisco if you travel though Phoenix, Dallas, and Denver, so it takes considerably longer to go from the end-user to the final destination if the data packets must transfer through four or five intermediaries.
- Tor encrypts the data between the intermediary nodes.
- Some intermediary nodes do not have high-bandwidth connections.
The following examples from an informal survey illustrate just how much Tor can slow down web browsing:
|
Domain |
Time for Direct Access |
Time for Tor Access |
|
cnn.com |
28.1 seconds |
188 seconds |
|
baidu.com |
2.2 seconds |
9.34 seconds |
|
google.de |
1.89 seconds |
7.5 seconds |
|
pff.org |
15.87 seconds |
74 seconds |
Note: The results of the speed test depend heavily upon the specific Tor route used. Stopping Tor and then re-enabling it would likely produce a materially different result since the speed of the intermediary and exit-nodes would likely be different.
While Tor is slow, it can be improved mildly by changing a number of default configuration options. See here, here, here and here.
Increased Vulnerability. The second major downside is that the exit-node could record your data or perform a number of malicious attacks, as explained by Ars Technica and SecurityFocus.com. As the Berkman Center’s 2007 Circumvention Report noted, “Tor provides strong anonymity only if the user is careful to submit data to HTTPS protected servers.” If you plan to use Tor, you should consult the following Tor security warnings:
- REMARK(S) ABOUT USING CONFIDENTIAL DATA ON (INSECURE) NON-HTTPS/SSL-CONNECTIONS: If you’re planning to visit password protected sites on non-encrypted connections, keep in mind that some exit-nodes record the passwords and possibly use them for abuse. Also all other transferred data is possibly recorded and misused.
- REMARK(S) ABOUT ACCESSING ELECTRONIC BANKING AND OTHER SENSITIVE SITES VIA TOR: Most banks and similar institutions (PayPal for example) are using extended fraud countermeasures, like IP-origin plausibility checks and anonymous server blacklistings. Therefore you risk getting your bank account locked for security reasons by using the Tor-network.
- REMARK(S) ABOUT (SECURE) HTTPS/SSL-CONNECTIONS TO FRAUD CRITICAL SITES: If you’re planning to visit fraud critical HTTPS/SSL-secured sites (Banks for example) and that specific site is querying you unexpectedly about accepting a new SSL-Certificate, be highly alert. Check the Certificate data or try another EXIT-node first. There are some rumors around, that some EXIT-nodes are trying to fake/highjack such HTTPS/SSL-connections.

 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.