 Every once and awhile it’s worth taking a step back and looking at the long view of how Internet policy developments have unfolded and consider where they might be heading next. We’ve reached such a moment as it pertains to efforts to police the Internet for copyright piracy, objectionable online content, privacy violations, and cybersecurity. We’re at an interesting crossroads in this regard since the prospects for successful cracking down on copyright piracy and pornography appear grim. Seemingly every effort that has been tried has failed. The Net is awash in online porn and pirated content. I am not expressing a normative position on this, rather, I’m just stating what now seems to be commonly accepted fact.
Every once and awhile it’s worth taking a step back and looking at the long view of how Internet policy developments have unfolded and consider where they might be heading next. We’ve reached such a moment as it pertains to efforts to police the Internet for copyright piracy, objectionable online content, privacy violations, and cybersecurity. We’re at an interesting crossroads in this regard since the prospects for successful cracking down on copyright piracy and pornography appear grim. Seemingly every effort that has been tried has failed. The Net is awash in online porn and pirated content. I am not expressing a normative position on this, rather, I’m just stating what now seems to be commonly accepted fact.
In the meantime, the United States is in the process of creating new information control regimes and this time its access to personal information and cybersecurity that are the focus of regulatory efforts. The goal of the privacy-related regulatory efforts is to help Netizens better protect their privacy in online environments and stop the “arms race” of escalating technological capabilities. The goal of cybersecurity efforts is to make digital networks and systems more secure or, more profoundly as we see in the Wikileaks case, it is to bottle up state secrets.
These efforts are also likely to fail. Simply stated, it’s a nightmare to bottle-up information once it’s out there. It doesn’t make a difference if that information we are seeking to control is copyrighted content, hate speech, dirty pictures, defamatory speech, secret diplomatic cables, or personal information. Information is the blood that runs through the veins of the Internet and once it’s out it is pretty much Game Over. Commenting on the recent Wikileaks debacle over the release of diplomatic cables, Wall Street Journal columnist Daniel Henninger noted that “There is one certain fix for the WikiLeaks problem: Blow up the Internet. Short of that, there is no obvious answer.” The same thing is increasingly true for these other types of information flows.
Now That’s A Lot of Information
As I pointed out in my recent essay, “Privacy as an Information Control Regime,” efforts to control information today are greatly complicated by problems associated with (1) convergence, (2) scale, (3) volume, and (4) unprecedented individual empowerment / user-generation of content. It’s the volume problem that I want to spend a bit of time on here today.
As I noted in that previous essay, the sheer volume of media and communications activity taking place today greatly complicates regulatory efforts. In simple terms, there is just too much stuff for policymakers to police today relative to the past.
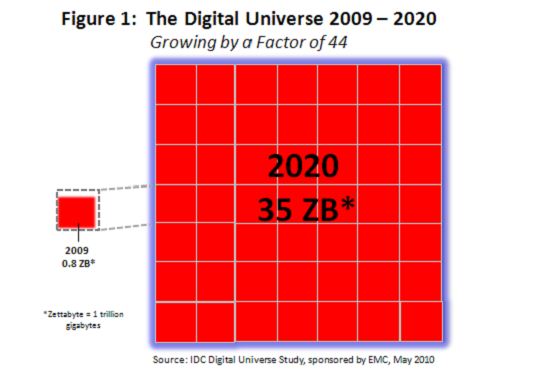
Let’s put some hard numbers on this problem. IDC’s 2009 report, “The Digital Universe Ahead — Are You Ready?” provides the following snapshot of the data deluge:
- Last year, despite the global recession, the Digital Universe set a record. It grew by 62% to nearly 800,000 petabytes. A petabyte is a million gigabytes. Picture a stack of DVDs reaching from the earth to the moon and back.
- This year, the Digital Universe will grow almost as fast to 1.2 million petabytes, or 1.2 zettabytes.
- This explosive growth means that by 2020, our Digital Universe will be 44 TIMES AS BIG as it was in 2009. Our stack of DVDs would now reach halfway to Mars.
And here’s a little something from the Global Information Industry Center’s report on “How Much Information?”:
In 2008, Americans consumed information for about 1.3 trillion hours, an average of almost 12 hours per day. Consumption totaled 3.6 zettabytes and 10,845 trillion words, corresponding to 100,500 words and 34 gigabytes for an average person on an average day. A zettabyte is 10 to the 21st power bytes, a million million gigabytes. These estimates are from an analysis of more than 20 different sources of information, from very old (newspapers and books) to very new (portable computer games, satellite radio, and Internet video). Information at work is not included.
(How about that caveat: information at work is not included!!)
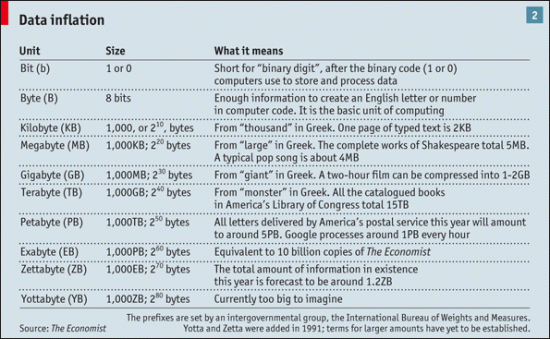
To put all these petabytes and zettabytes in some context, here’s a chart that appeared in an Economist essay back in February entitled, “All Too Much: Monstrous Amounts of Data“:
These are mind-boggling numbers. As the Economist chart suggests, it’s hard to even fathom what “yottabytes” entails, but that’s what’s next.
Anyway, let’s return to the privacy wars and think about the volume problem in that context. Today we’re hearing proposals to regulate online services (advertising networks) or software (web browsers) to clamp down on the flow of information. The so-called “Do Not Track” mechanism is one potential solution that has been floated in the regard.
This reminds me of the illusive search for a “simple fix” or silver-bullet solution to online pornography. The PICS /ICRA experience is instructive in this regard. That would be the W3C’s Platform for Internet Content Selection and Internet Content Rating Association. For a time, there was hope that voluntary metadata tagging and content labeling could be used to screen objectionable content on the Internet. But the sheer volume of material to be dealt with made that task almost impossible. The effort has been abandoned now. Of course, it’s true that effort didn’t have a government mandate behind it to encourage more widespread adoption, but even if it would have, does anyone really think all porn or other objectionable content would have been labeled and screened?
Similar problems await information control efforts in the privacy realm, even if a mandated Do Not Track mechanism required the re-engineering of web browser architecture. Those who think Do Not Track would slow the “arms race” in this arena are kidding themselves. If anything, a Do Not Track mandate will speed up that arms race. Take a look at how well The CAN SPAM Act worked in practice if you want another example.
Selective Morality
Now, let’s pretend for a moment that I am wrong about all this in the privacy space and that the FTC and Congress somehow find a workable mechanism to control flows of personal information and can clamp down accordingly. Again, I don’t believe it will happen, but if it did, doesn’t that mean it’s equally likely that the same mechanism would be used to crack down on speech, expression, copyrighted content, state information flows, or whatever else?
Perhaps that’s not a bad thing from your perspective, but what I find entertaining about this debate is how the folks who support an aggressive information control regime for privacy purposes generally also oppose information control efforts as it pertains to speech, expression, copyright, or state secrets. There’s a bit of selective morality at play here. When it comes to personal information, the attitude seems to be that we must ‘pay any price, bear any burden,’ even going so far as to property-tize personal information flows. In every other case, however, the attitude seems to be: Let information flow.
Regardless of one’s disposition on these matters, my point here is more simple: the information will flow. Indeed, I think it is safe to say that there is a strong and growing negative correlation between the aggregate volume of data flowing across digital networks and the ability of policymakers to control those information flows. The recent Wikileaks release has made that new fact of life more evident to the world, but the ongoing IP wars might also hold some lessons for us in this regard.
Consider the thoughts of Sydney-based consultant Mark Pesce, who compares the two experiences. He writes:
We’ve been here before. This is 1999, the company is Napster, and the angry party is the recording industry. It took them a while to strangle the beast, but they did finally manage to choke all the life out of it – for all the good it did them. Within days after the death of Napster, Gnutella came around, and righted all the wrongs of Napster: decentralized where Napster was centralized; pervasive and increasingly invisible. Gnutella created the ‘darknet’ for filesharing which has permanently crippled the recording and film industries. The failure of Napster was the blueprint for Gnutella.
In exactly the same way – note for note – the failures of Wikileaks provide the blueprint for the systems which will follow it, and which will permanently leave the state and its actors neutered.
And it is likely a blueprint for what will happen in the privacy arena as well.
Conclusion
Again, I want to be clear that the point of this essay has not been to endorse or celebrate copyright piracy, widespread porn, privacy violations, release of state secrets, etc. We’ll all have differences of opinions on these matters. But there’s simply no getting around the fact that all these problems are all likely here to stay and, barring extreme crackdowns, it’s very hard for me to imagine how government might reverse that tide.
In the extreme, I suppose we could follow the Chinese mode and firewall off digital networks, effectively nationalize ISPs, and then pay citizens to inform on each other about various transgressions. Or, we could impose punishing forms of liability on digital intermediaries — effectively deputizing online middlemen and making them servants of the State. But such extreme solutions would have nightmarish ramifications for the future of the Internet and digital communications networks. We have to ask ourselves how far we want to go to control information flows.

 The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.
The Technology Liberation Front is the tech policy blog dedicated to keeping politicians' hands off the 'net and everything else related to technology.